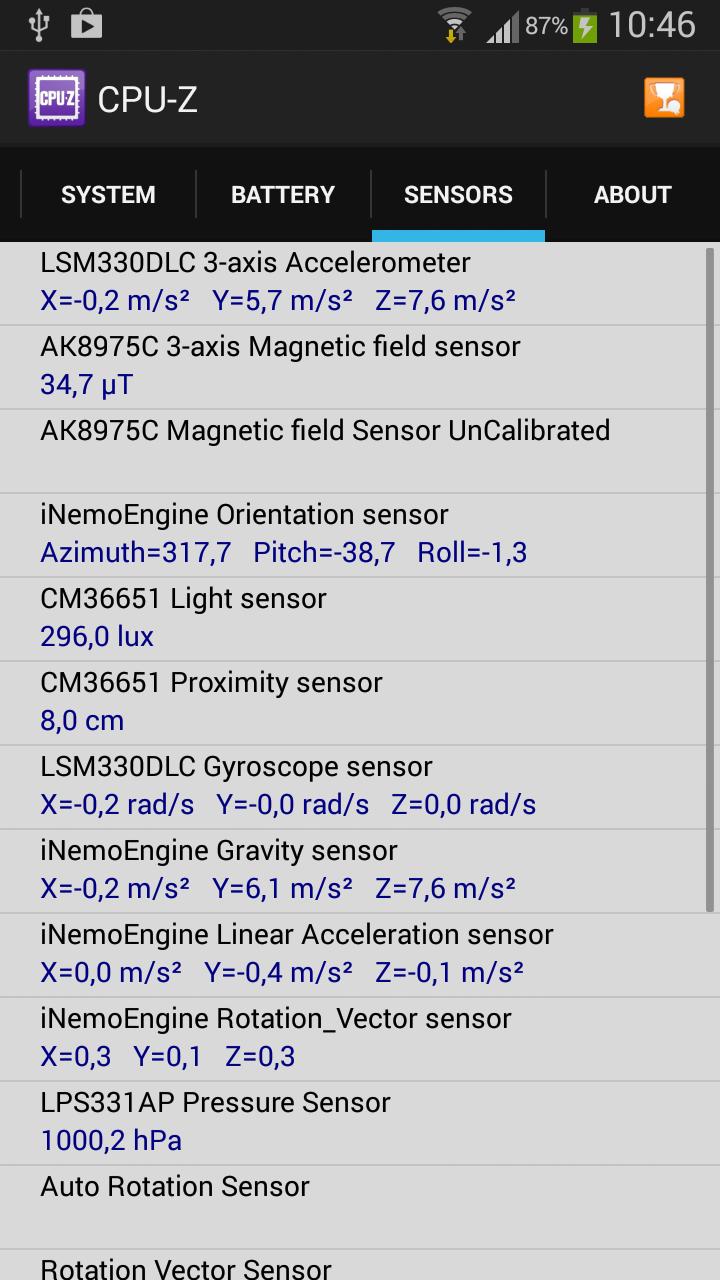
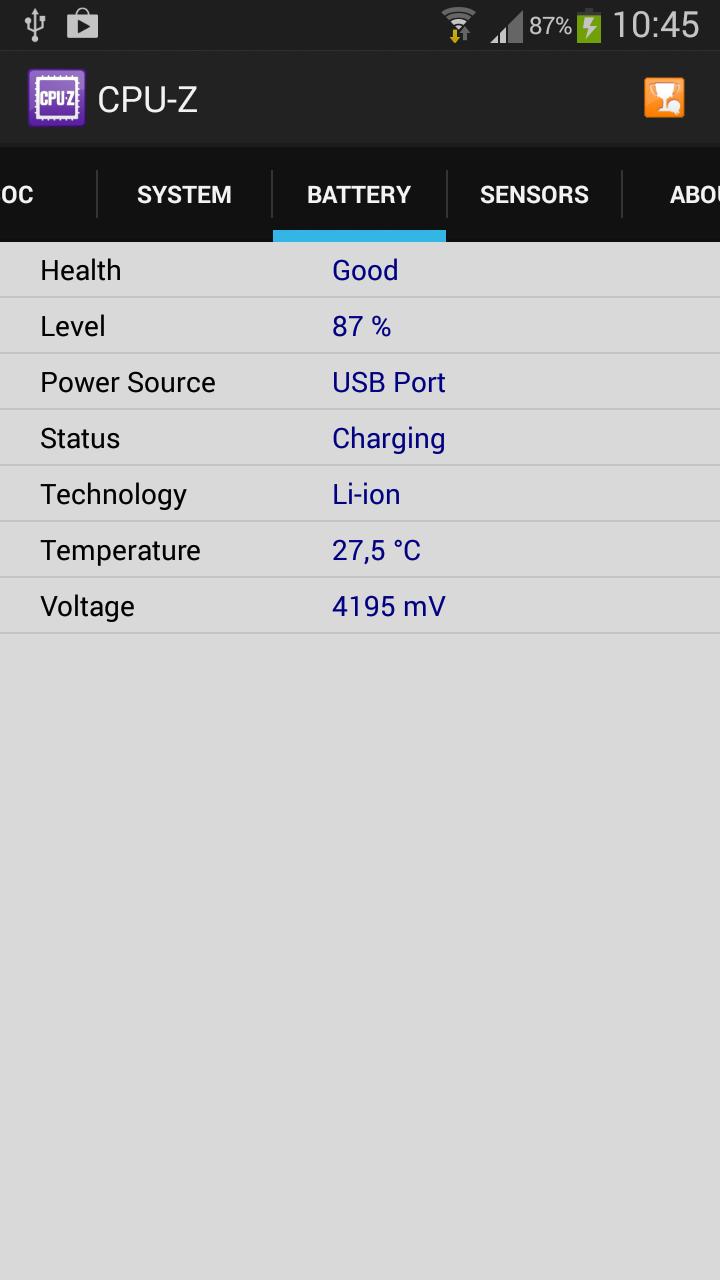
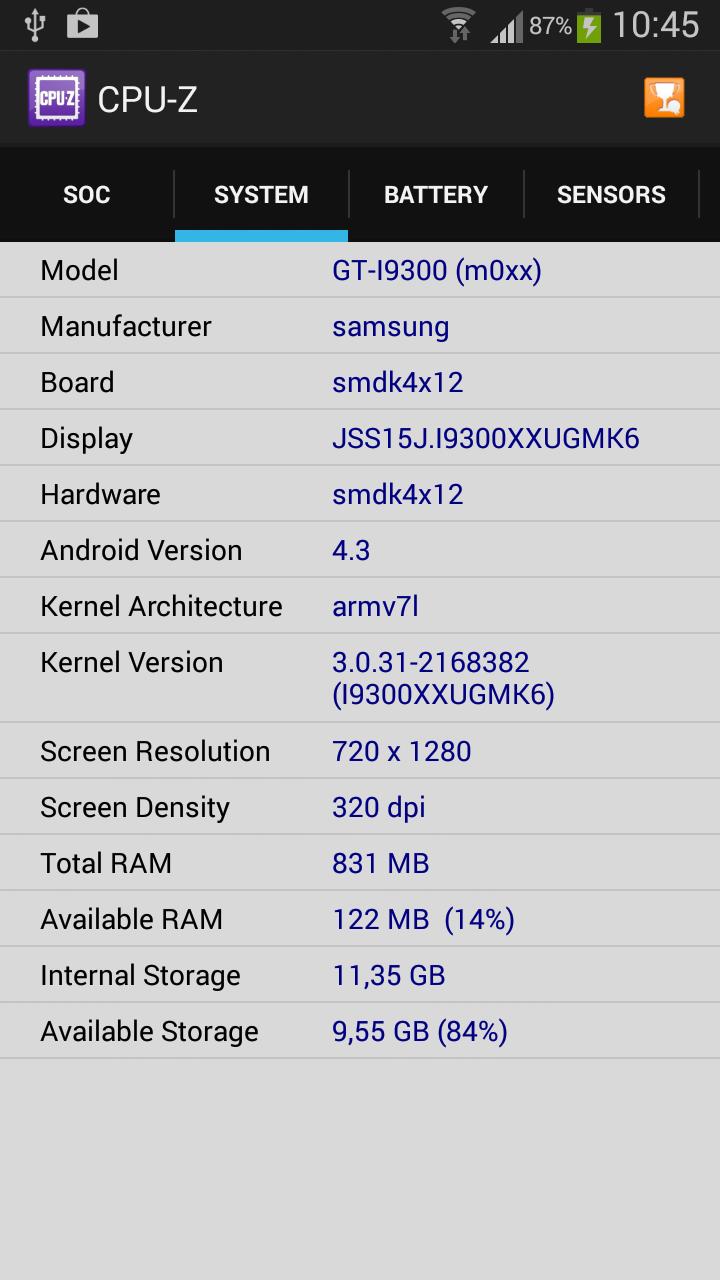
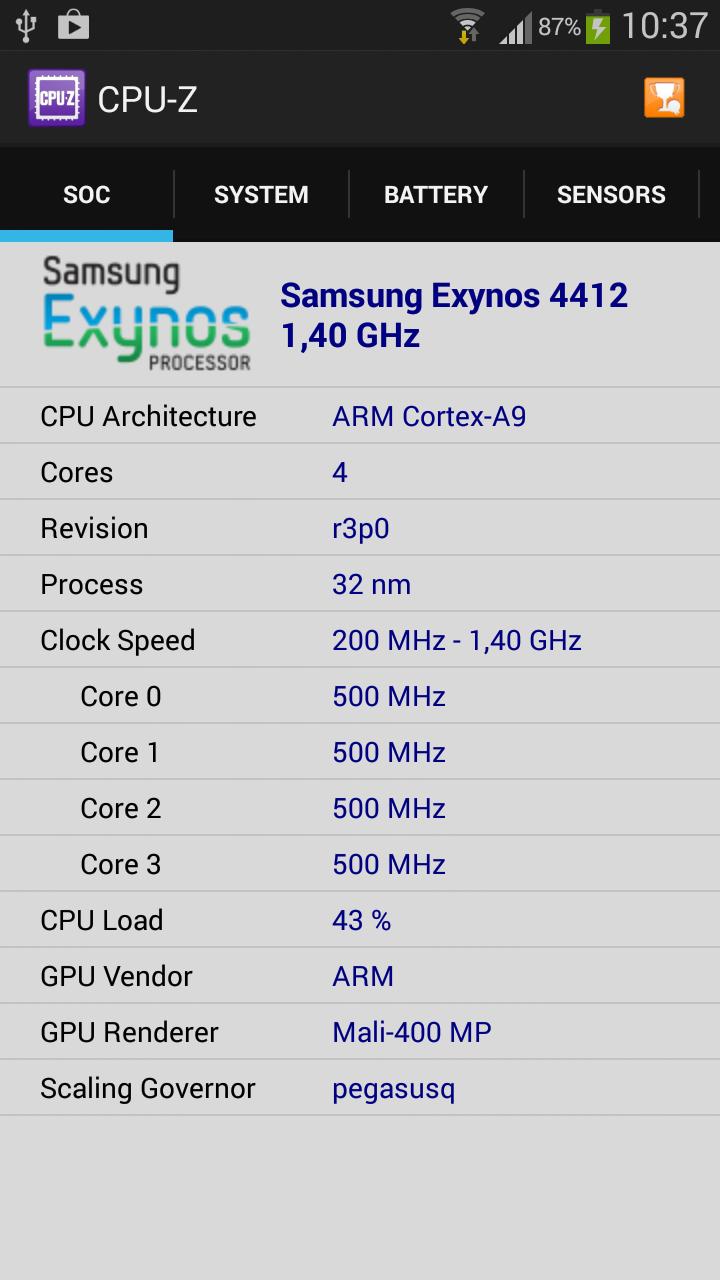
Introduction:
CPU-Z is a powerful and widely recognized application designed for anyone looking to dive deep into the hardware specifications of their PC, whether it's a laptop or a desktop. With its extensive capability to provide detailed information about your processor, motherboard, RAM, and graphics card, CPU-Z stands out as an essential tool for tech enthusiasts and professionals alike.Main Features:
- Comprehensive Hardware Information: Access vital details about your processor, including model, voltage, lithography, frequency, cache memory, and socket type.
- Motherboard Details: Discover your motherboard's exact model, PCI-Express technology support, chipset, and BIOS version.
- RAM Insights: Evaluate RAM frequency, latencies, XMP profile application, and operating voltage for optimal performance monitoring.
- Graphics Card Specs: View essential information such as model, lithography, GPU chip, memory frequency, memory technology, and bus width.
- Benchmarking and Stress Testing: Use built-in benchmarking tools to assess processor performance in single and multithreaded tasks, as well as stress tests to verify overclock stability.
Customization:
While CPU-Z is primarily data-driven, users can customize their settings to best reflect their monitoring preferences. Adjust the display options for easier reading and tackle advanced functionalities based on your hardware configuration.Modes/Functionality:
- Benchmark Mode: Test your processor's capabilities against industry standards.
- Stress Test Function: Evaluate system stability under various loads, especially for those experimenting with overclocks.
Pros and Cons:
Summary of the app's strengths and areas for improvement.Pros:
- Detailed hardware information for comprehensive analysis.
- User-friendly interface suitable for both beginners and advanced users.
- Effective benchmarking and stress testing features.
- Lightweight application, requiring minimal system resources.
Cons:
- Limited customization options in data display format.
- Advanced features may be overwhelming for novice users.
Frequent questions
Is CPU-Z secure?
Yes, CPU-Z is a totally secure program. It only provides information about your computer's hardware and does not allow you to make changes to settings such as frequencies or voltages that make your system unstable. However, the Benchmark section does include a stress test that can cause your PC to reach high temperatures.
Is CPU-Z useful?
Yes, CPU-Z is a very useful software developed by the French company CPUID. CPU-Z supports most processors and motherboards on the market, thanks to which you can know the hardware data of very old or very new computers because its database is always up to date.
Is the information provided by CPU-Z reliable?
Yes, the information provided by CPU-Z is totally reliable. You can check if you have overclocked a component properly, know the exact model number of a product, or view your motherboard's chipset to find out if you can replace the processor with a better one.
What hardware data does CPU-Z let you know?
CPU-Z lets you know in-depth details of a PC's hardware, including its processor, graphics card, RAM and motherboard data. Among the available data, you can find frequencies, voltages, exact models, and much more.
Available For Other Platforms
Discover more apps
MagiKart: Retro Kart Racing lets you race as various characters, using customizable controls and special items, evoking nostalgia reminiscent of Super Mario Kart.
LunaProxy offers stable residential proxies for social media, with 200 million devices, dynamic pricing, 99.9% uptime, easy API integration, and a profitable affiliate program.
Genius DLL is an easy-to-use application for quickly downloading and registering DLLs, requiring just a few clicks to search, download, and manage libraries.
The Quick Start tab in Google Chrome provides access to installed apps, including a shortcut for iCloud Reminders, enhancing user convenience despite being unofficial.
Tiger Password Recovery is a user-friendly tool that efficiently retrieves lost passwords across various applications and devices using advanced algorithms.
Desktop Gadgets Revived restores classic Windows desktop gadgets, allowing customization with functional and aesthetic widgets on modern operating systems, maintaining compatibility and nostalgic design.
Advanced BAT to EXE Converter transforms BAT files into EXE format, enhancing application protection and aesthetics while allowing versioning and password features for developers.
Renee File Protector is a tool that easily hides and locks files on your computer or external devices, ensuring sensitive information remains secure.